I wish we hadn’t used all the keys on the keyboard.
Bill Joy
The Atreus is about a reduced set of keys.
I’ve been using the Atreus keyboard for three years. Three years! Time flies. I want to get around to posting something about this keyboard for a while now; I finally got around to write something.
Back in 2020 I kickstartered the Atreus keyboard. At the beginning of October 2020 I held it in my hands and was able to try it out first time.
The Atreus is a small form factor 40% split keyboard keyboard. The original design by Phil Hagelberg had 42 keys and is open source hardware. The kickstarter project was a collaboration between Phil Hagelberg and keyboard.io which features 44 keys. It is also open source hardware and is freely programmable with open source software. Now the keyboard is offered in the online shop of keyboard.io. Keyboard.io offers great and easy to use configuring software called Chrysalis (also open source). It’s easy to start and configure your keyboard to your needs. Advanced users can even flash their own firmware. Which is needed for advanced concepts like tap dance.

I originally was interested in the keyboard because of slight wrist pain, which soon went away after using the Atreus. The slight angle at which the halves of the keyboard are arranged help the wrists to stay straight whilst typing. The fact that it’s Open source, hardware and software was a big bonus. The reduced key set seems like a hindrance at first, but is really an advantage in reducing the movement of your hands while using the keyboard. It is no longer necessary to move your elbows or shoulders when accessing numbers, special characters, or arrow keys. Even multimedia keys are at a fingers reach.
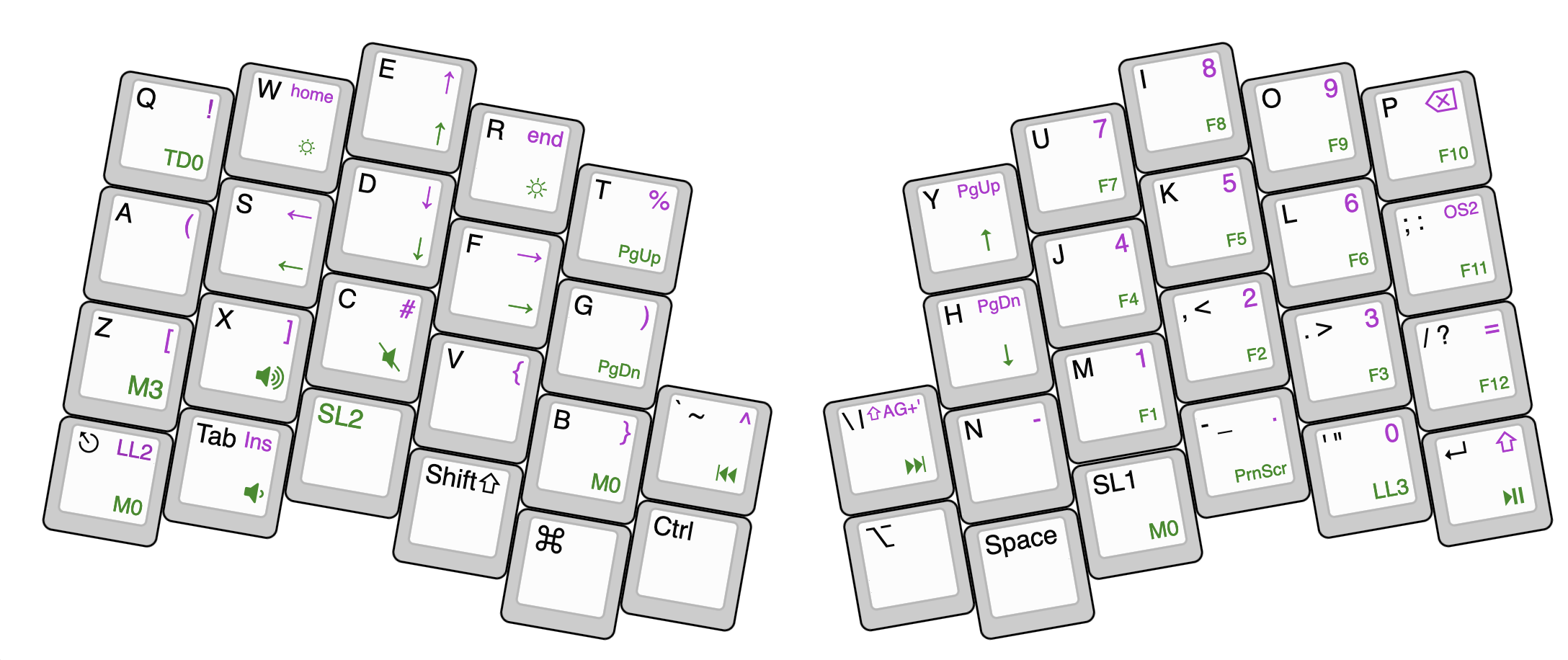
The Atreus offers the user the configuration of multiple layers to access every key a full sized keyboard would offer. The standard configuration it’s great but can easily be changed with the Chrysalis software.
When I recently broke my arm I really came to appreciate the easy configurability of the Atreus. I was able to configure a one hand layout to the right side of the keyboard, which allowed me to access every key of the keyboard and type in a painless fashion. This reconfiguration is the trigger for my writing. I wanted to offer a configuration for people who might have a similar problem.
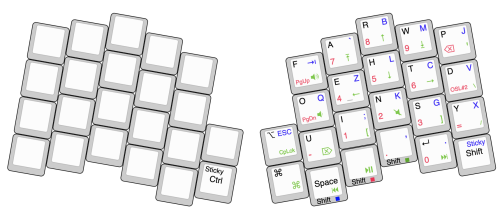
My basic letter layout is inspired by the now discontinued frog pad. The most frequent letters are placed on layer zero, the rest only one. Special characters, modifiers, and multimedia keys placed in a way that allow a convenient control. The num pad is reused from my standard layout. I don’t think I’m done with tweaking the layout, but it’s a great first start. Typing speed is still not where it was with two hands. I’m looking forward to using the Atreus with both hands again.
I really can recommend this nifty little keyboard.

You can find my current configuration on Gitlab.